Microsoft office is something i guess everybody uses it and knows about it and you are a regular computer user then to somewhat extent you are definitely going to use Microsoft office or any other variant, so in this particular post we want to show you how malicious documents can be analyzed in order to find malicious macro code. so let's start it.
Malicious Samples
Macro Code is usually written in vba programming for more on it just see the wiki. here i have some malicious sample files which you can get by asking me in comments. they contain some macro code which basically just pings localhost and opens notepad.exe on a windows host.
 |
| malware asking for enable macro |
so how do we about finding what lies in the code? go to excel options and then check the developer tab.
 |
| show developer tab |
so it'll show us the developer tab, in developer tab click on visual basic and it should show you the vba macro code.
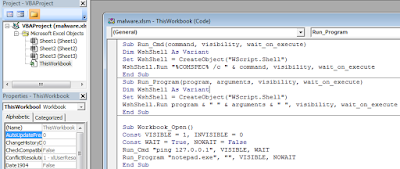 |
| macro code |
now we can look at it and find what it's doing but what if we get kind of a document which cannot show us macro then how we identify it. here is a little python code i wrote to extract macro and some analysis options from a specific file.
and below is the result.
 |
| extract_vba |
Boom, we can see what the macrocode is and analysis shows what exactly its going to do, okay let's see another approach. if you have installed clamav it contains a package sigtool which can extract macro code as well from any binary. yes binary :) see below screen shot.
 |
| sigtool --vba Binary |
That's it hope you've enjoyed it. Please see the video if you were lost somewhere.
No comments:
Post a Comment